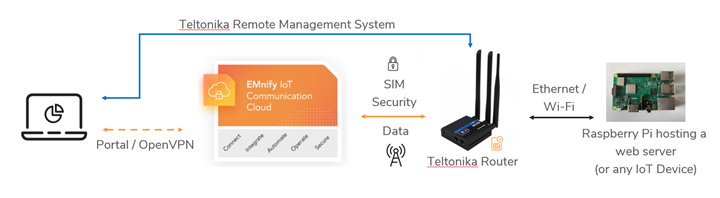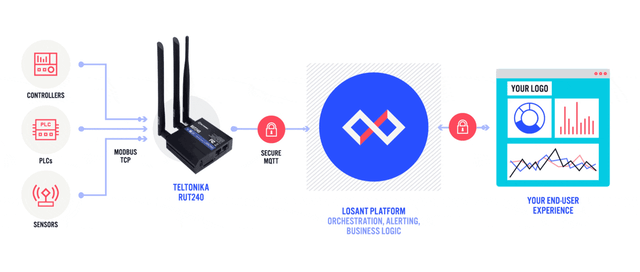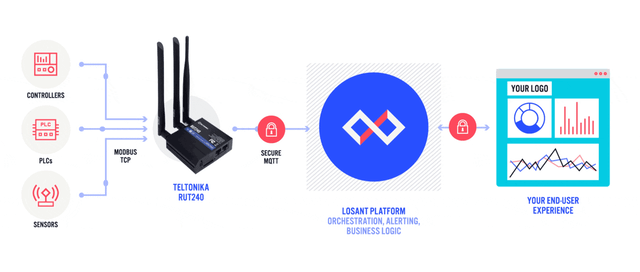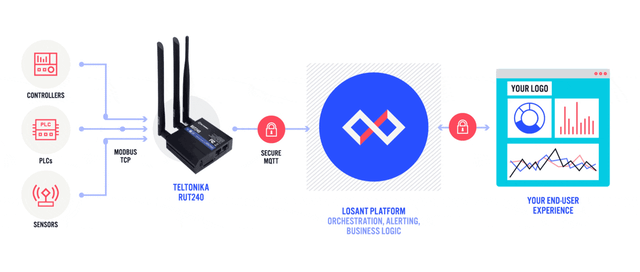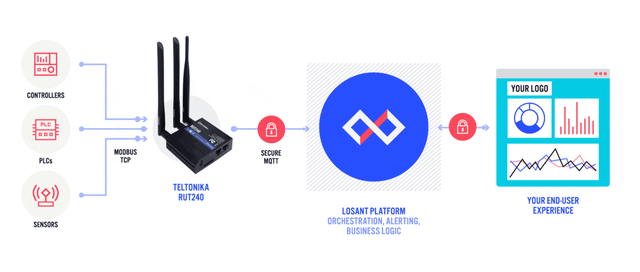
Sensors | Free Full-Text | Automated IoT Device Identification Based on Full Packet Information Using Real-Time Network Traffic
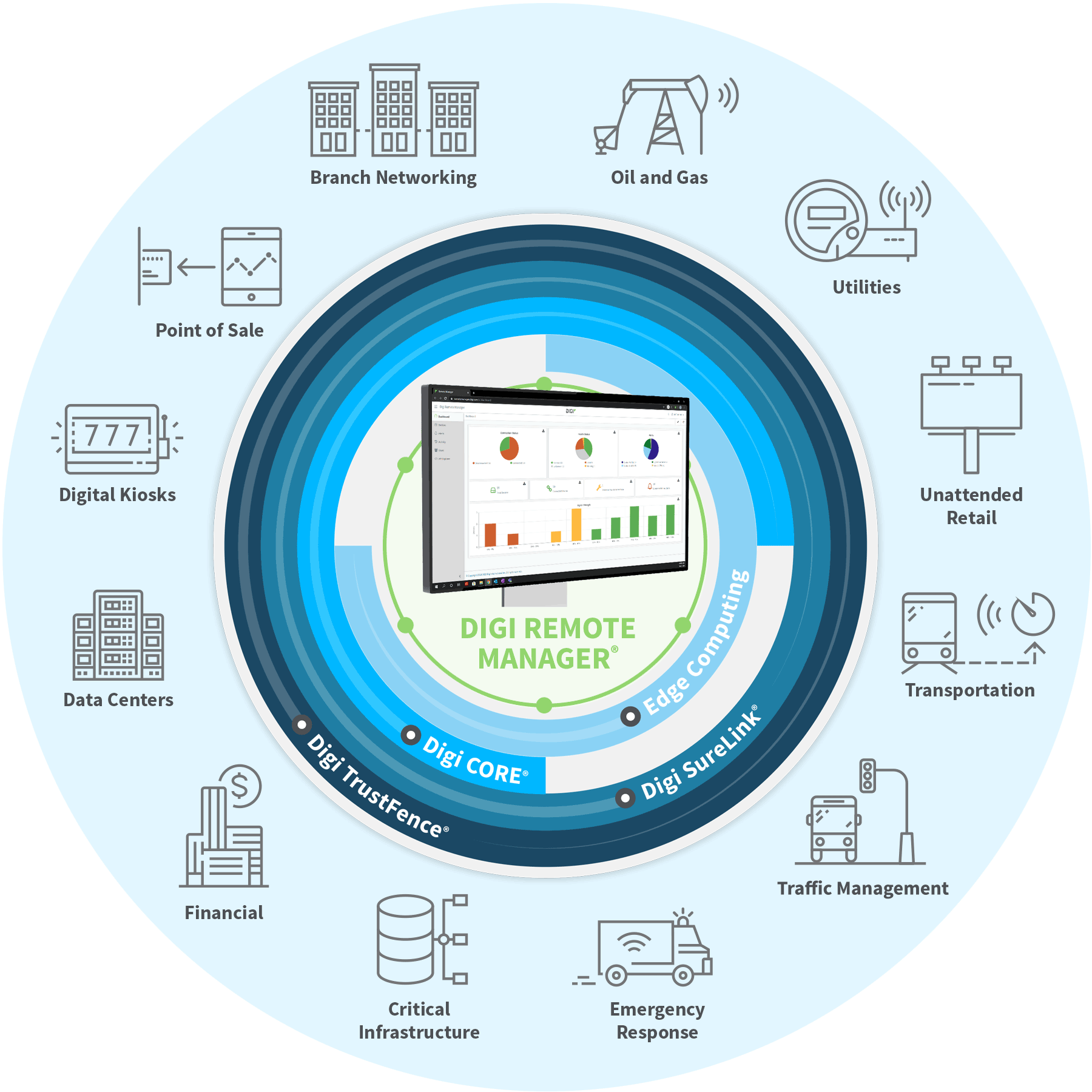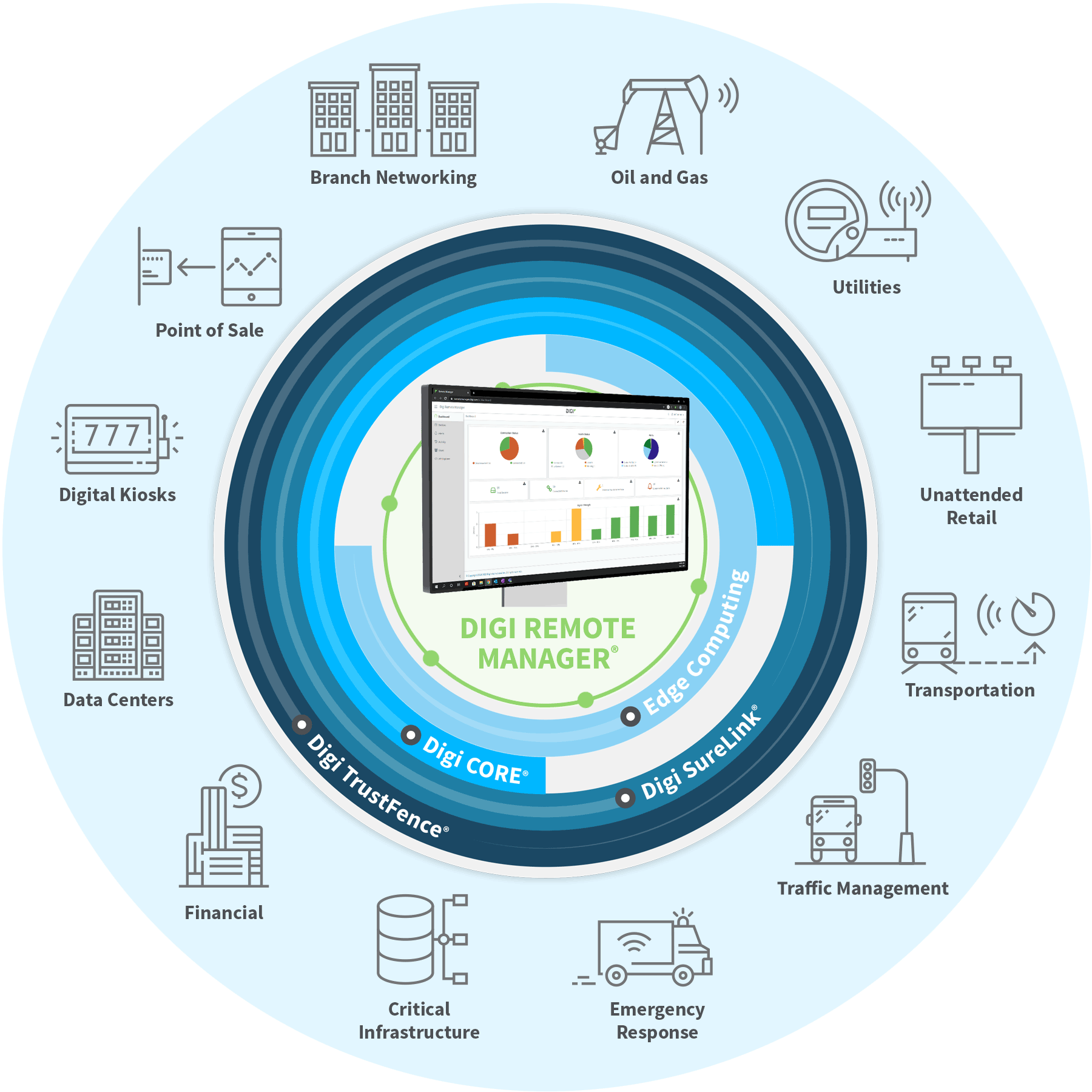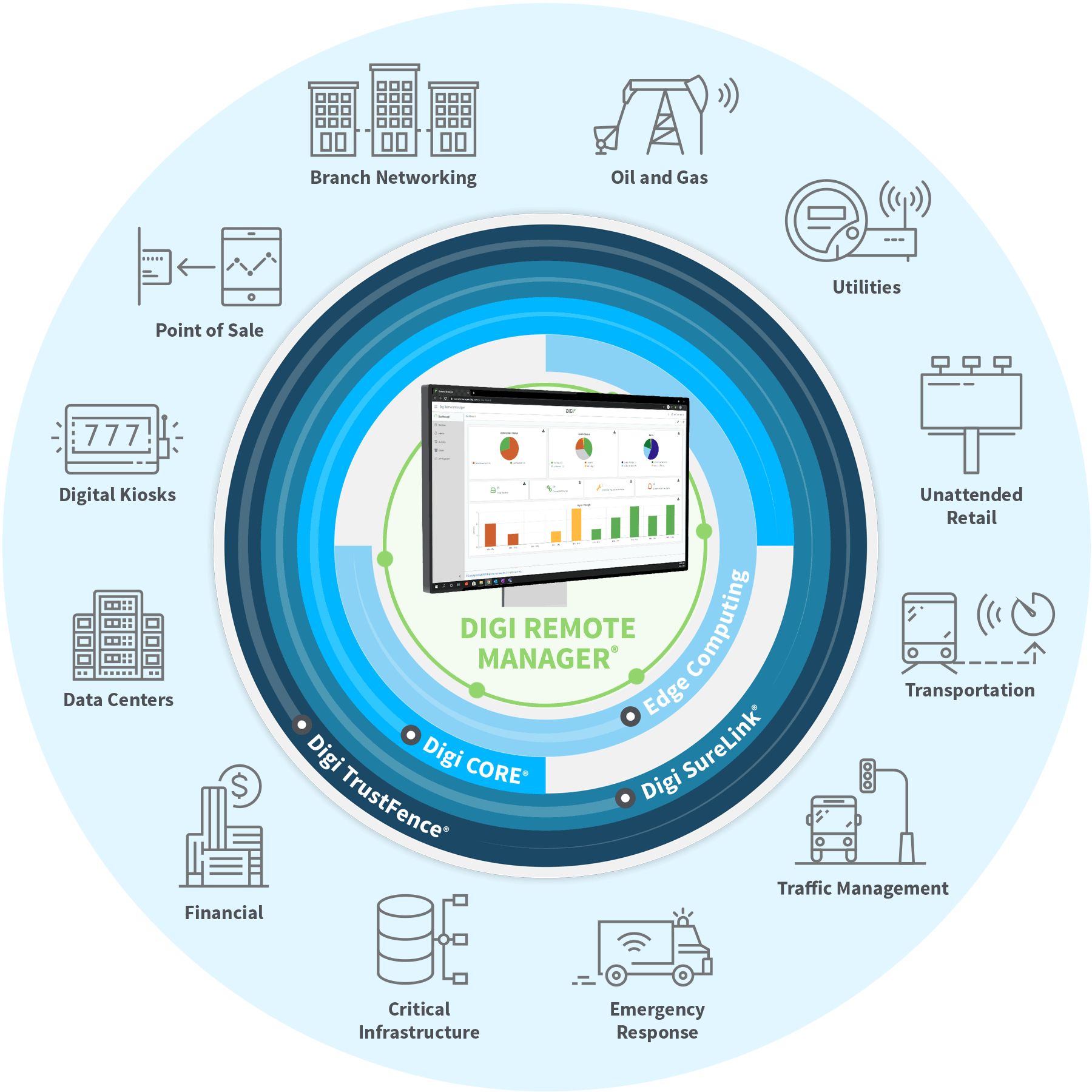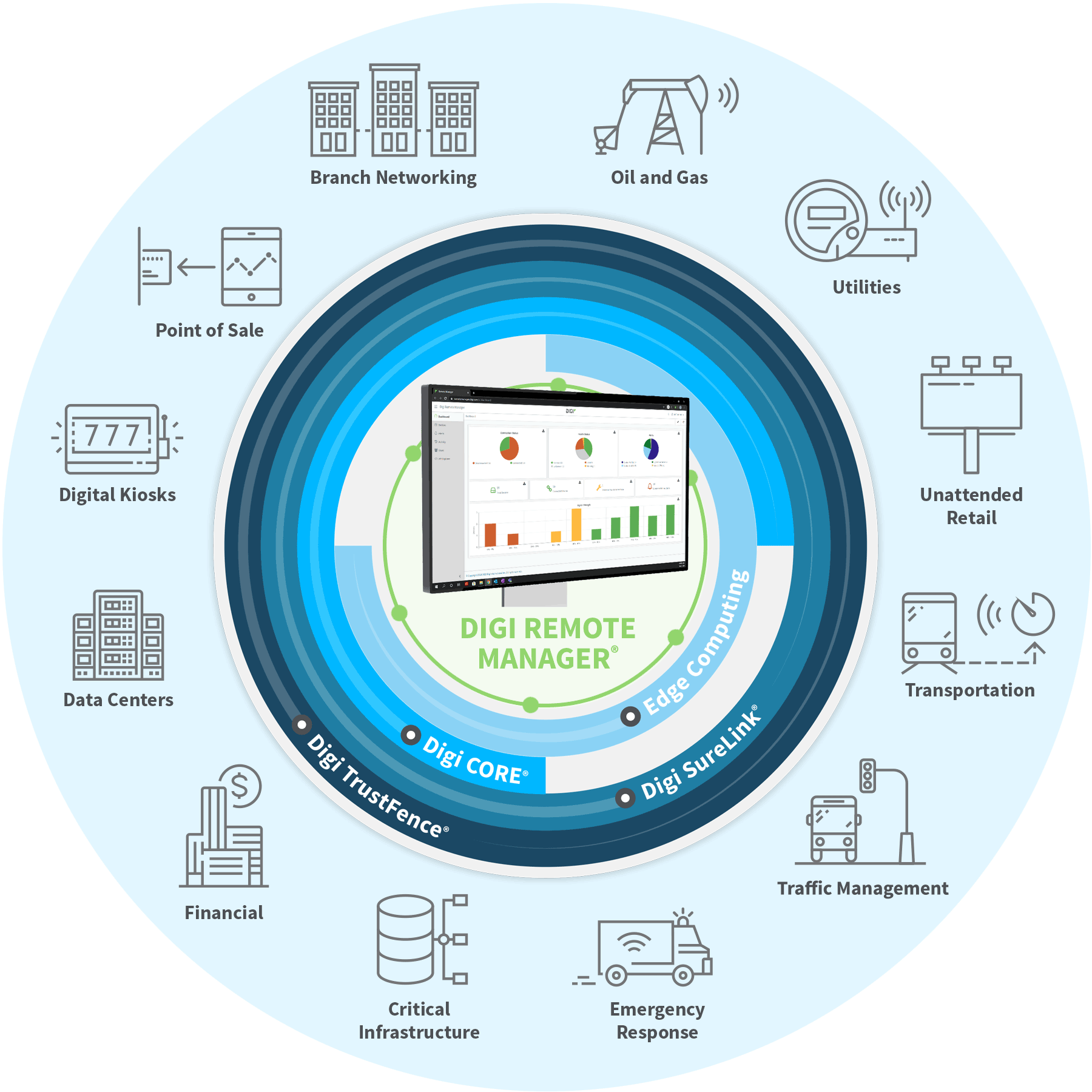
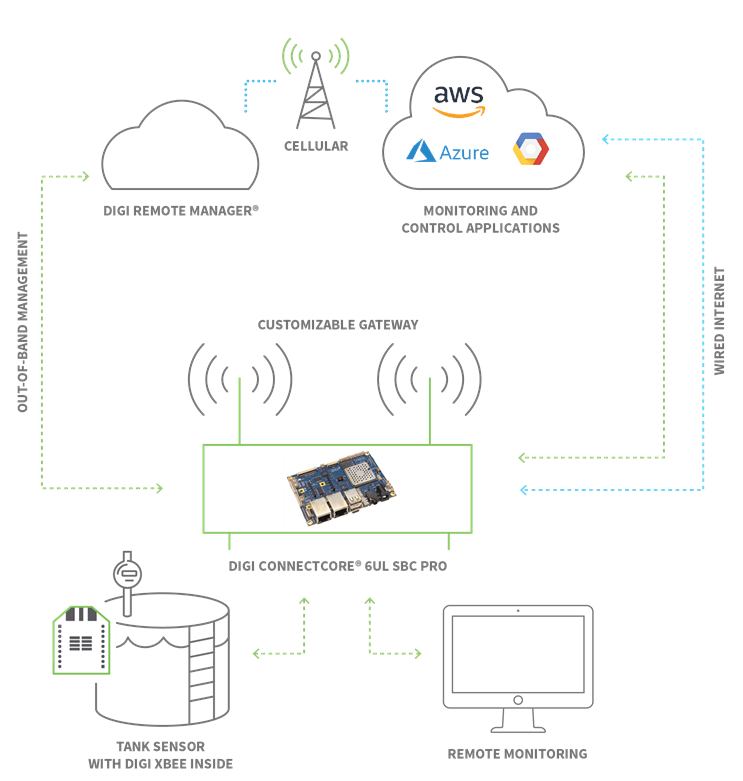
IoT Device Monitoring - Centralized Remote Device Management Solution - Digi Remote Manager | Digi International
![How to Provide Secure Remote Access to IoT Edge Devices via Web, SSH and Remote Desktop | macchina.io Blog [Staging] How to Provide Secure Remote Access to IoT Edge Devices via Web, SSH and Remote Desktop | macchina.io Blog [Staging]](https://macchina.io/blog/wp-content/uploads/2021/11/remote-iot-device-access.png)
How to Provide Secure Remote Access to IoT Edge Devices via Web, SSH and Remote Desktop | macchina.io Blog [Staging]

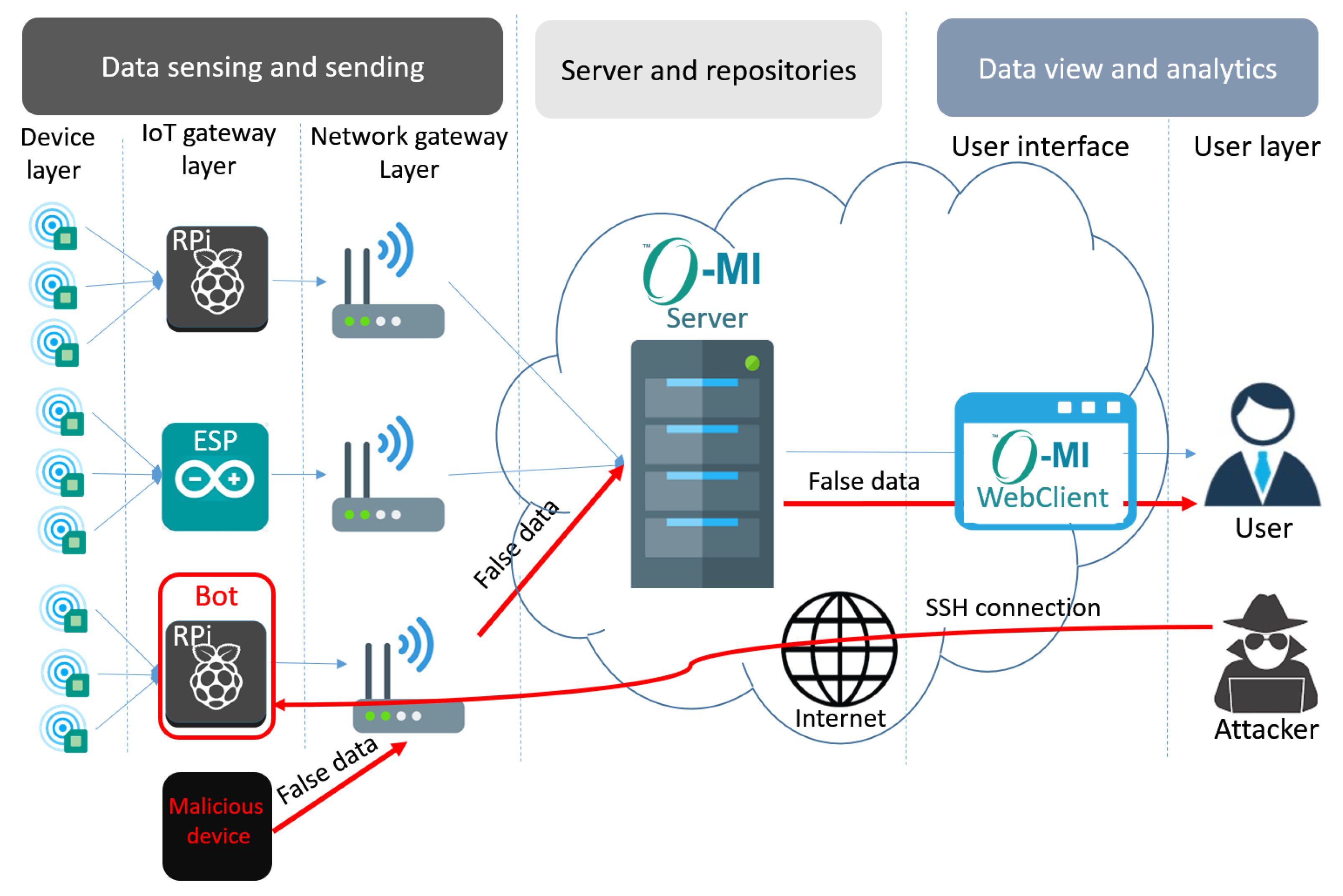
Threat model: an IoT device communicates with a server in the Internet;... | Download Scientific Diagram

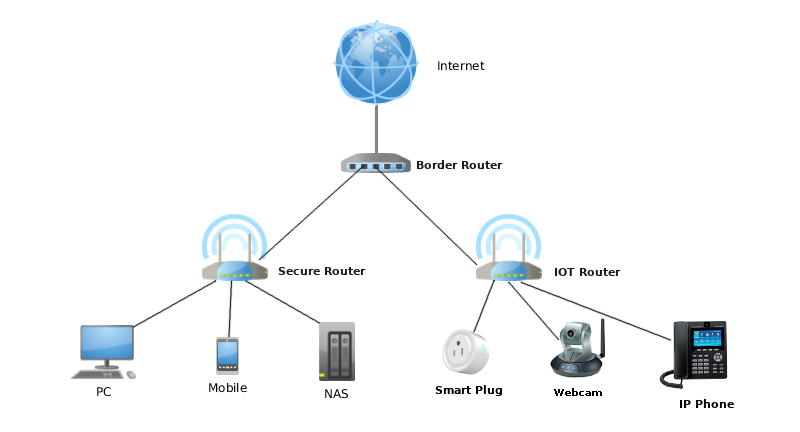
Remote SSH into IoT devices or Raspberry Pi behind NAT router or firewall from outside network over the internet | by Ganesh Velrajan | Medium

7 patterns for IoT data ingestion and visualization- How to decide what works best for your use case | The Internet of Things on AWS – Official Blog