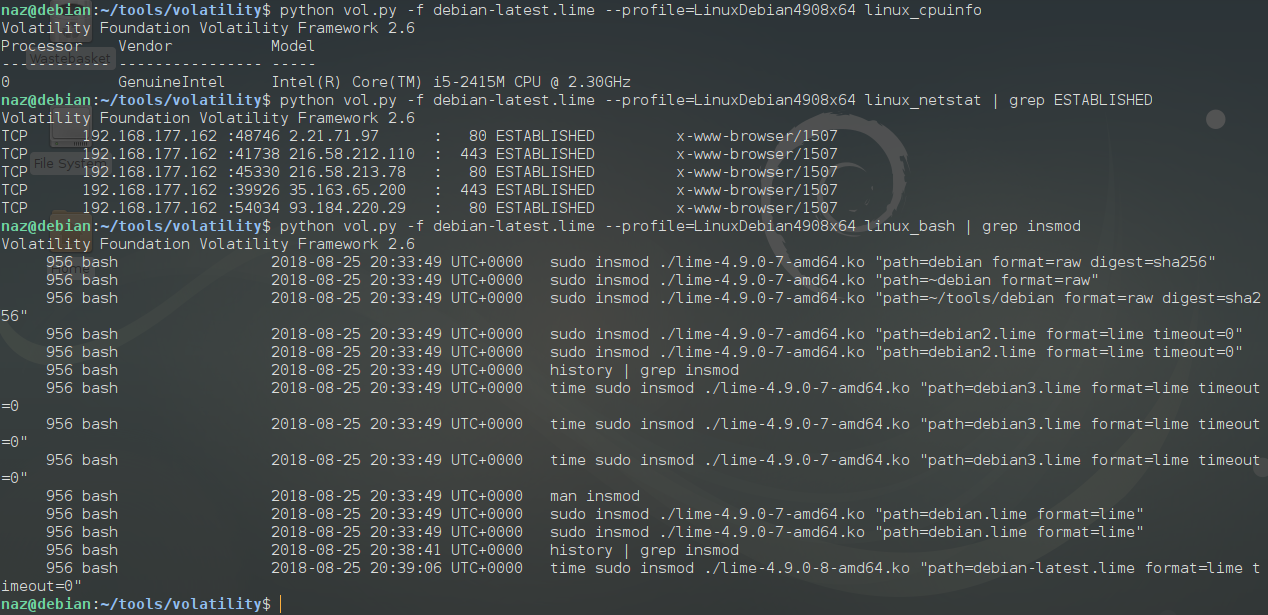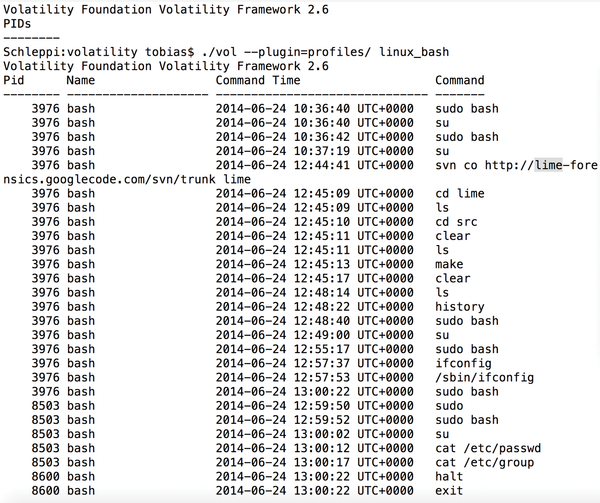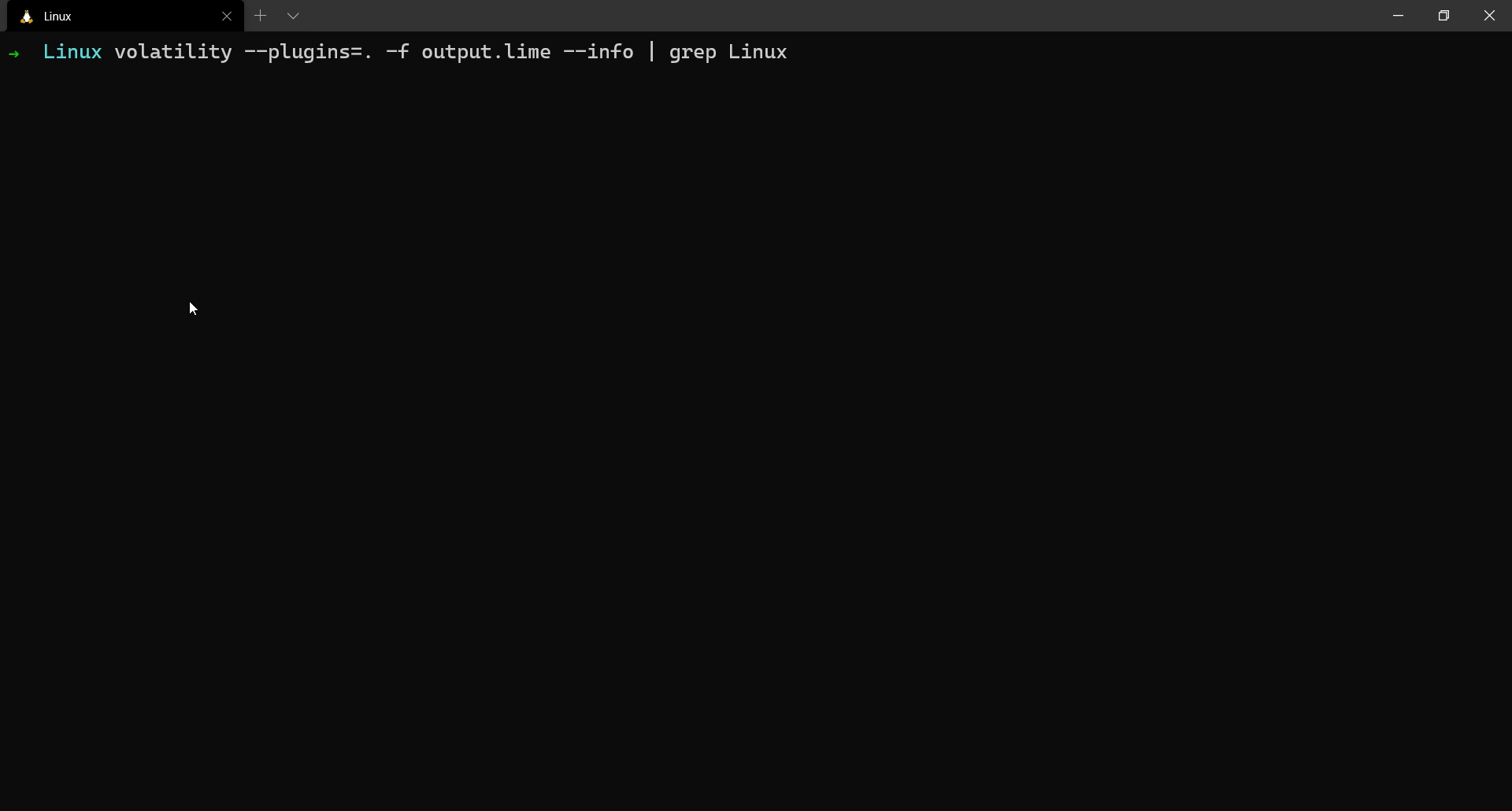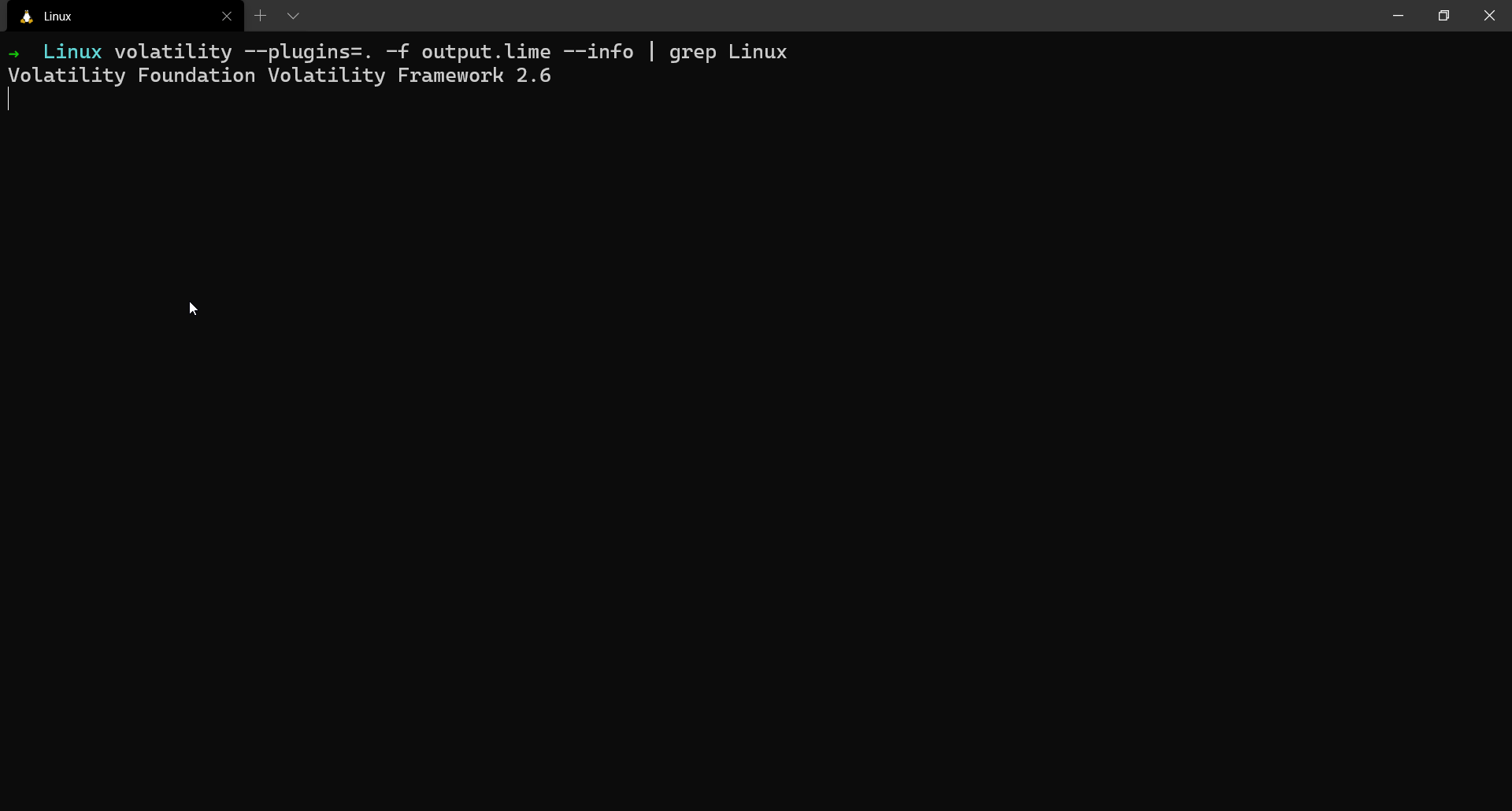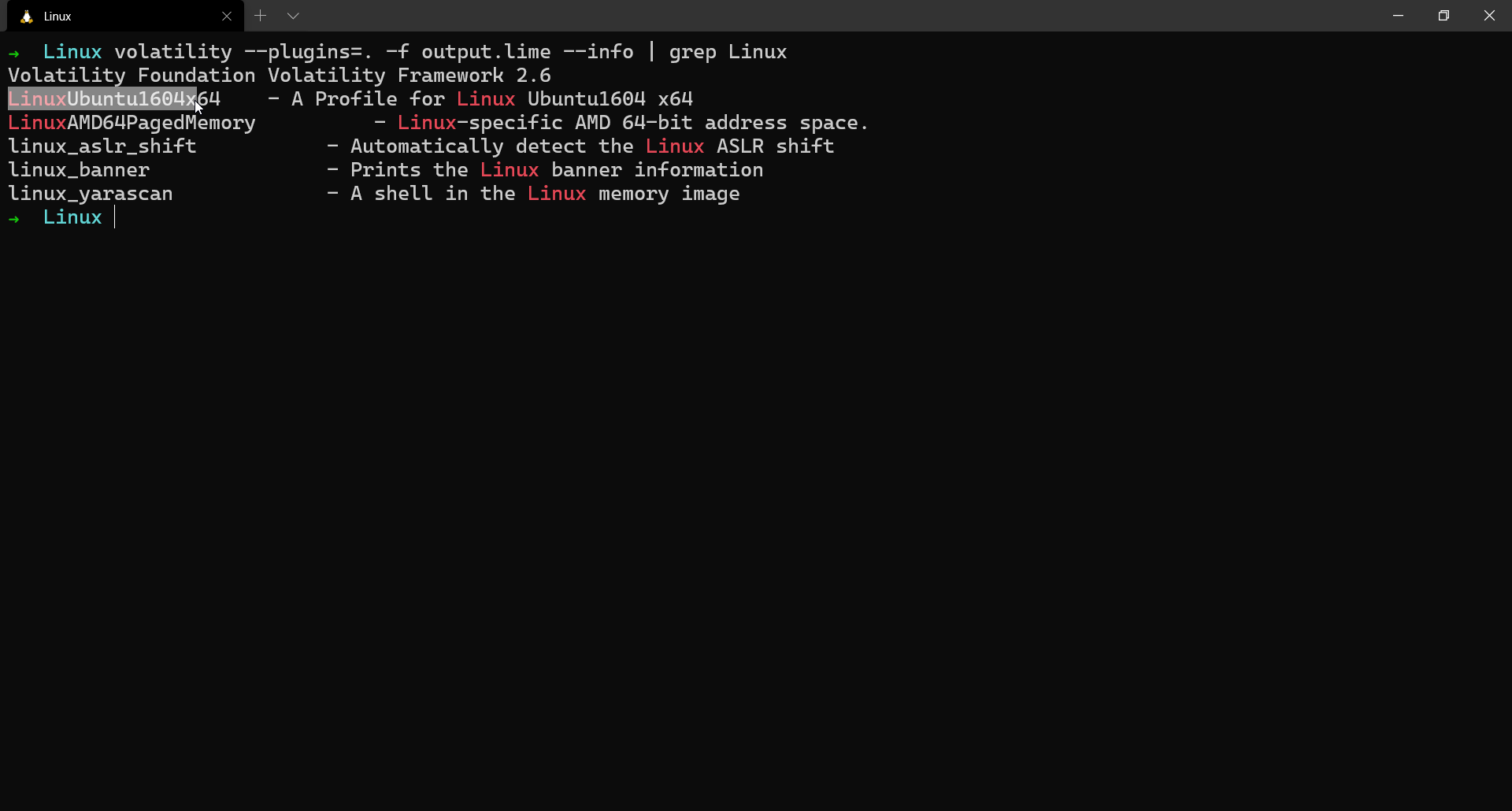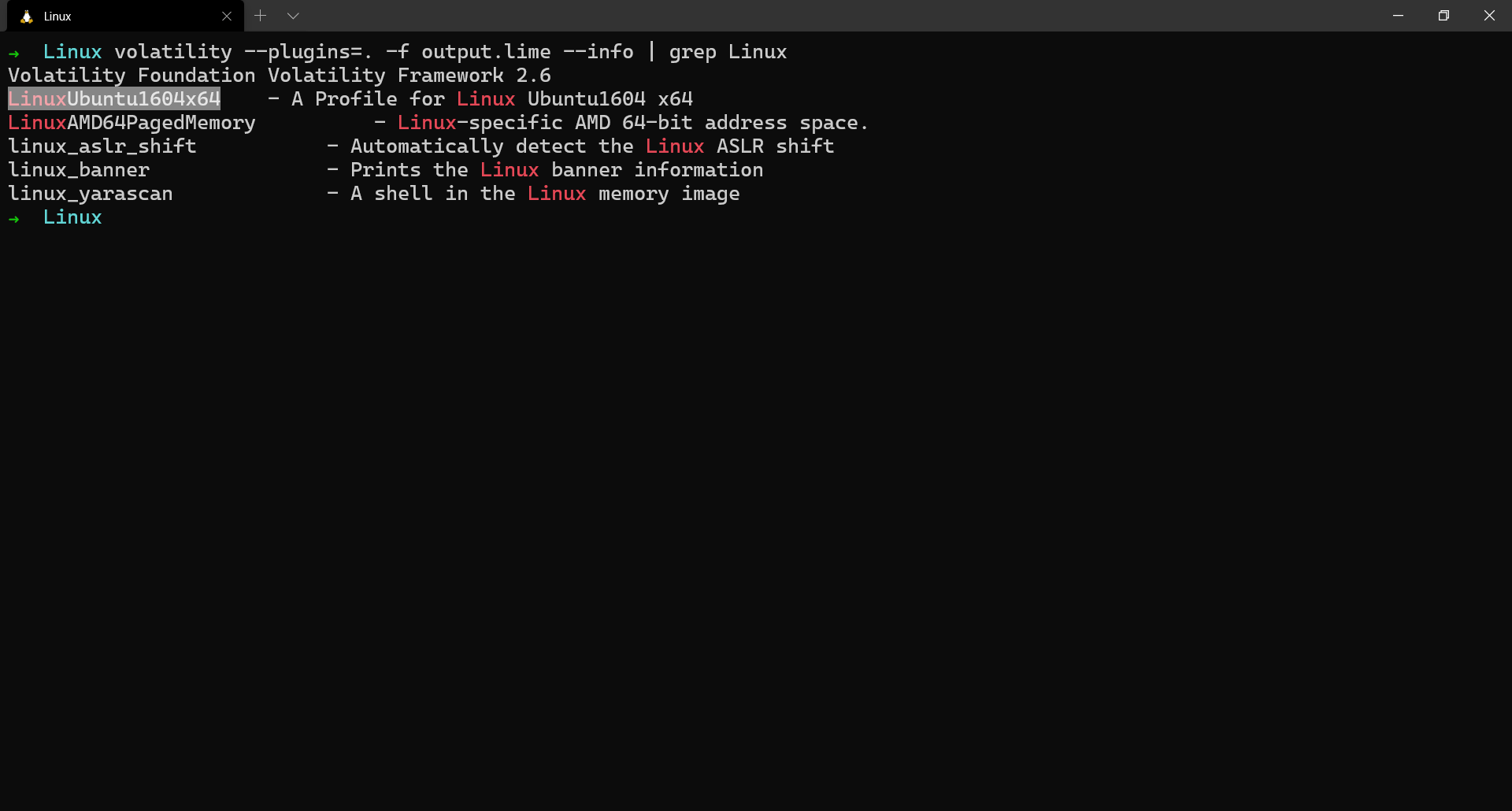
Volatility Framework - Advanced Memory Forensics Framework - Darknet - Hacking Tools, Hacker News & Cyber Security

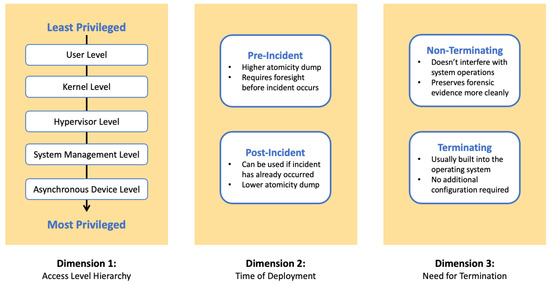
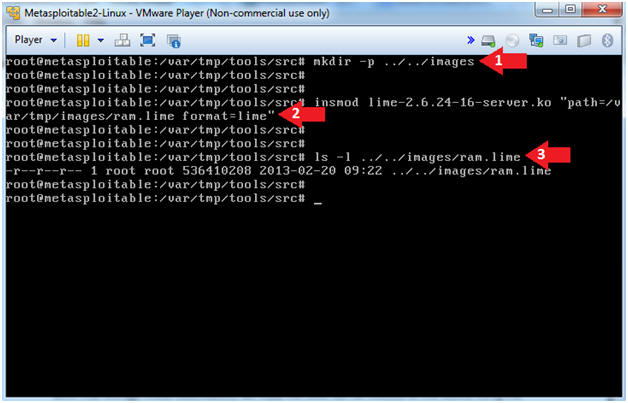
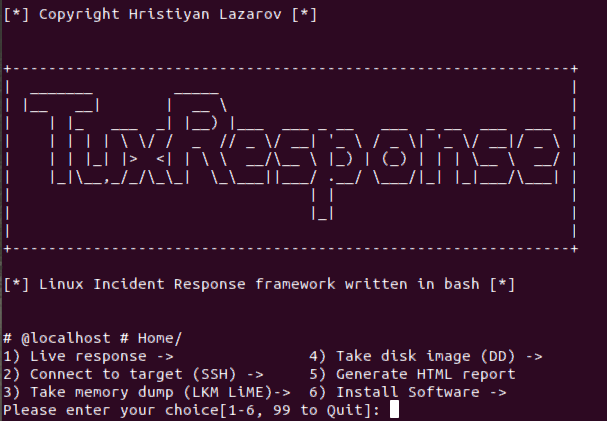
Open Security Research: Acquiring volatile memory from Android based devices with LiME Forensics, Part I
GitHub - 504ensicsLabs/LiME: LiME (formerly DMD) is a Loadable Kernel Module (LKM), which allows the acquisition of volatile memory from Linux and Linux-based devices, such as those powered by Android. The tool
![PDF] DroidScraper: A Tool for Android In-Memory Object Recovery and Reconstruction | Semantic Scholar PDF] DroidScraper: A Tool for Android In-Memory Object Recovery and Reconstruction | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/b1bc357462507d681fa90054381057e331574abb/4-Figure1-1.png)